Meeting key information security challenges
Protects corporate emails from targeted phishing and letters containing malware
Protects the network perimeter, services, and user workstations from a malware
Protects infrastructure from being controlled by external attackers
Secures the transfer of files from untrusted to trusted file storages
Detects network anomalies
Protects workstations and servers from potentially unwanted apps and untrustworthy devices
“Sees” more than others
- Detection of previously unknown threats based on Threat Intelligence & Attribution data. Proactive search for anomalies, hidden tunnels, and signs of communications with C&C servers.
- Automated correlation of events and alerts, and subsequent attribution to malware type and/or threat actor
- Global proactive threat hunting that exposes adversaries’ external infrastructure, TTPs, intent, and plans
- Proprietary tools: network graph analysis and malware detonation platform provide data enrichment, correlations, and analysis
- Full overview of the attack, in-depth management of incidents (up to Mutex/Pipes/Registry/Files)
- Detection of attacker infrastructure on a global scale
Technology conceived to collect a large amount of data and unique search algorithms designed to find connections help detect infrastructure that hackers intend to use in future attacks
Forrester Consulting TEI study
How a customer achieved 272% ROI and almost $1.9 million in benefits over three years with Group-IB Threat Hunting Framework
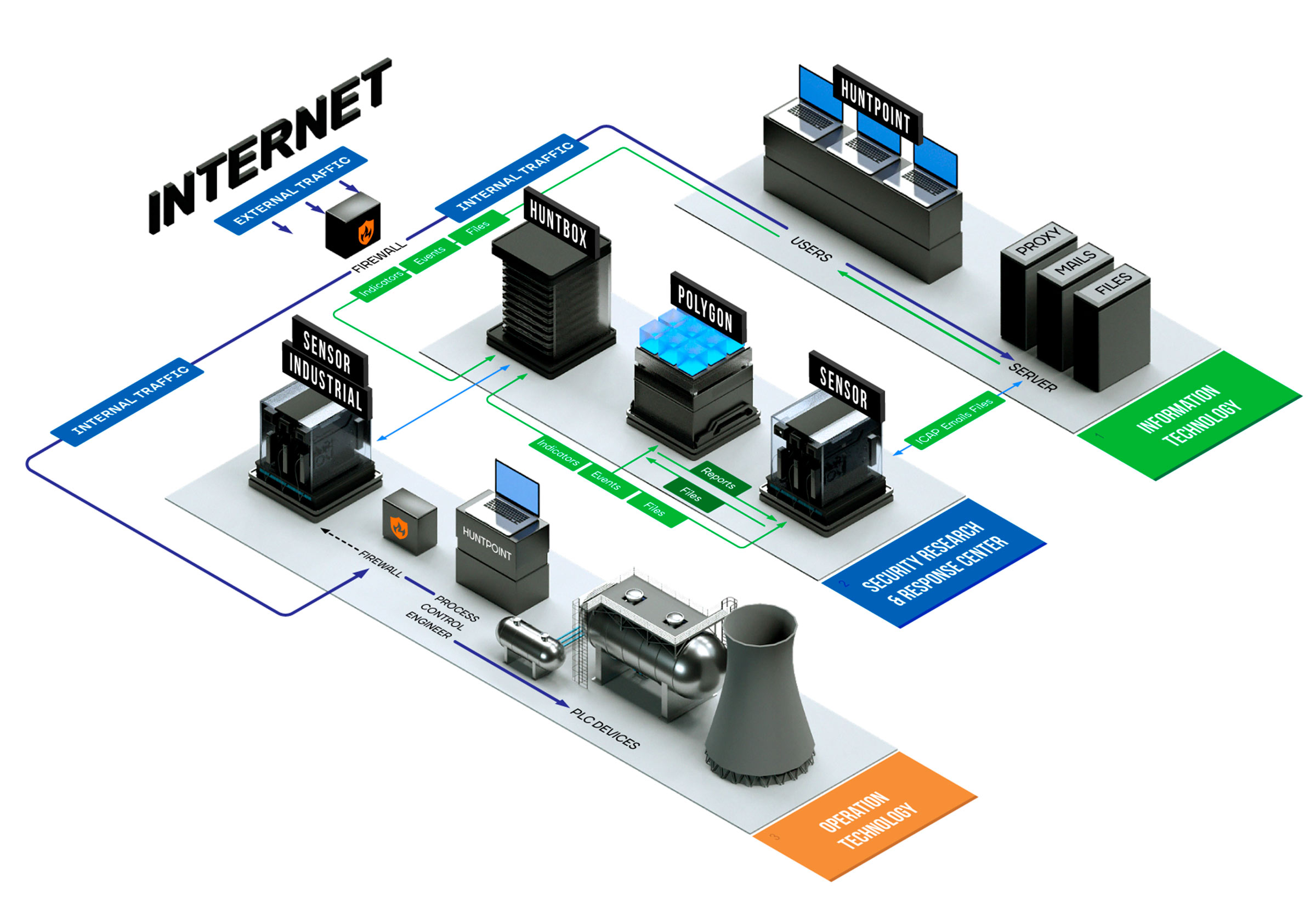
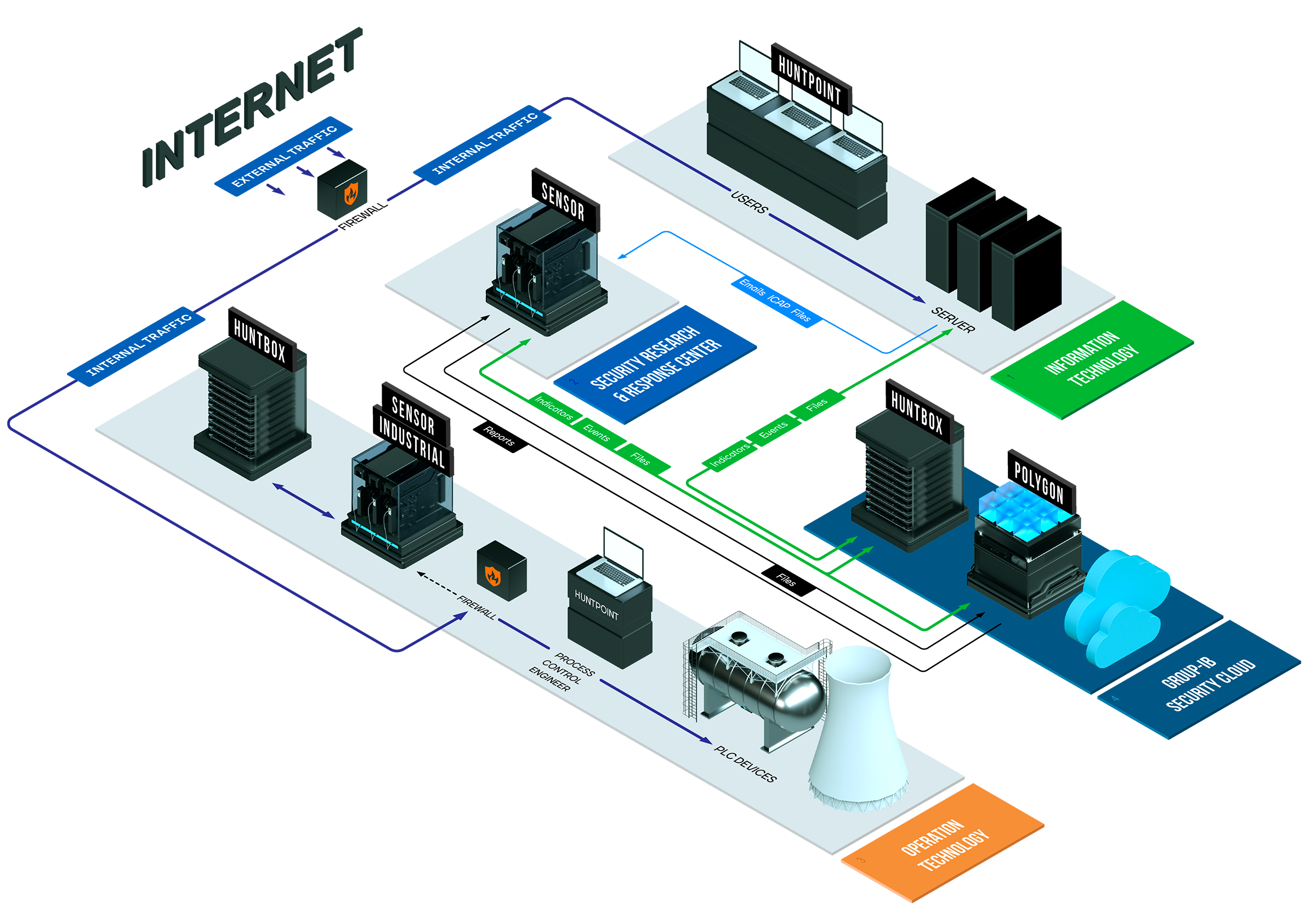
Group-IB Threat Hunting Framework (THF) modules
Managed detection & response 24/7
CERT-GIB
- Alert monitoring
- Anomaly analysis
- Threat Hunting
- Remote response
- Incident management
- Critical threat analysis
Detecting infrastructure management & data analysis
Huntbox
Collaborative Hunting & Response Platform
- Internal Threat Hunting
- Retrospective analysis
- Module management
- Single interface
- External Threat Hunting
- Correlation & attribution
- Data storage
- Event analysis
Attacks detection & prevention
Sensor
Network Research & Protection
- Traffic analysis
- File extraction
- Anomaly detection
Polygon
Malware Detonation & Research
- Isolated environment
- File analysis
- Link analysis
Huntpoint
Behaviour Inspection & Host Forensics
- Event logging
- Threat detection
- Response at hosts
Sensor Industrial
Analysis of industrial control systems
- Traffic analysis
- Support for industrial protocols
- Collection of information on firmware versioning
- Software integrity control
Decryptor
Decrypting TLS/SSL traffic in the protected infrastructure
Different usage scenarios
Threat monitoring & detection >
Understanding attackers and their tools helps identify even the most complex threats
Identification of complex attacks and tools:
Spearphishing campaigns, social engineering techniques, legitimate utilities, and other tools used by advanced groups
Coverage of the main infection vectors:
Email, browsers, removable media, local networks, client applications, supply chain attacks
Detection of infected mobile devices:
THF detects mobile Trojans when a device is connected to a corporate Wi-Fi network
Infrastructure protection >
At the client’s request, the solution can be configured to block threats in real time
Email protection:
When set in inline mode, the solution analyzes files and links in an isolated environment and blocks malicious objects spread by email
File storage protection:
When integrated with file storage systems, the solution detects and blocks malicious files before they are launched in a real environment
Traffic protection:
When integrated via ICAP THF can block malicious files downloaded from the internet
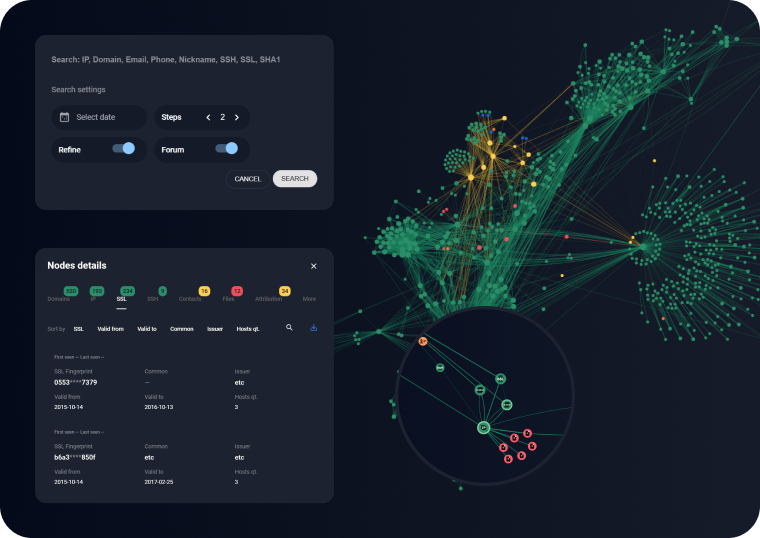
Threat Hunting Framework (THF) is your local center for research, detection, and response
Monitoring by Group-IB’s Computer Emergency Response Team
Threat Hunting Framework capabilities
Management of complex incidents
Discovers anomalies, hidden communication channels. Performs behavioral analysis for software and users, and event correlation.
Malware detonation and analysis
Patented technology performs dynamic analysis of malware in isolated environments on virtual machines and fully executes malicious code and extracts IoCs.
Collaboration with experts
Provides shared environment, remote incident response, digital forensics, and access to analysts and cyber community
Proactive threat hunting
Hunts on hosts within and outside the network perimeter while also analyzing the infrastructure of external adversaries
Access to threat intelligence
Attributes scattered events to specific malware types and families or certain cybercriminal groups for efficient attack termination.
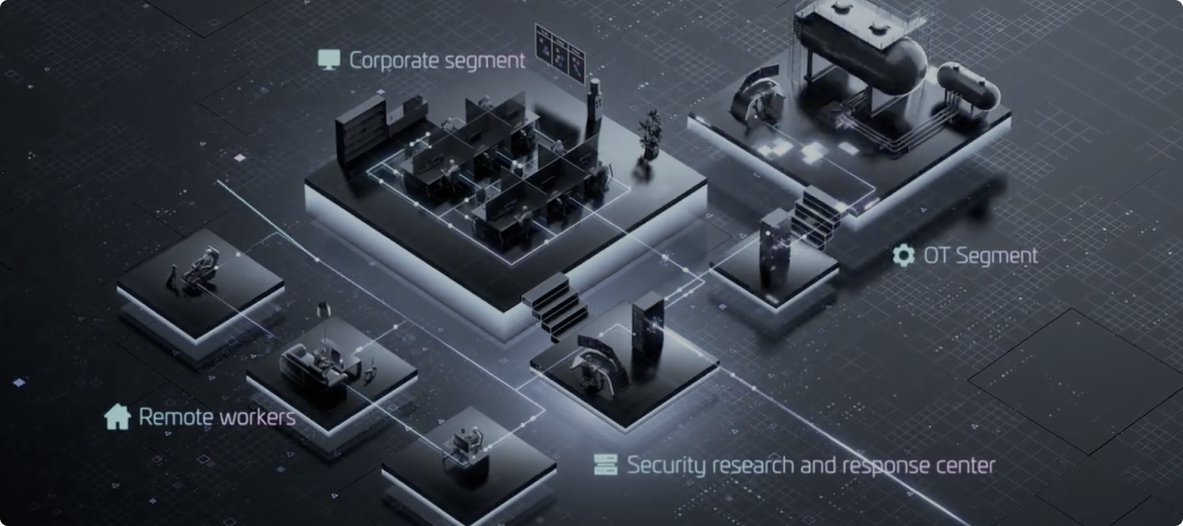
Unified security solution for IT and OT
A single system contains all the necessary tools for adaptive automation of research, threat hunting, and IR.
Additional benefits
- Representative visualization of incidents
- Management of all components from a single window
- Full context and in-depth analysis
- Clear account of event types and timelines
- Full support 24/7/365
- Most issues resolved within 10 minutes
Group-IB Threat Hunting Framework International Awards

Gold winner - Advanced Persistent Threat Protection (APT)

Gold winner - Anti-Malware

Gold winner - Critical Infrastructure Security

Gold winner - Threat Hunting

Gold winner - Anti-Phishing

Gold winner - Email Security

Gold winner - Endpoint Detection and Response

Gold winner - Endpoint Security

Gold winner - ICS / SCADA Security

Gold winner - Network Detection and Response

Gold winner - Network Security

Gold winner - Network Traffic Analysis

Gold winner - Ransomware Protection

Gold winner - Threat Detection, Intelligence and Response
Group-IB THF in reports and reviews

Network Detection and Response
KuppingerCole Analysts AG Names Group-IB a Product Leader for Threat Hunting Framework
Helpnetsecurity review
Threat Hunting Framework delivers on the promise of working on various layers (network, email system, files, endpoints, cloud) and providing actionable analytics from incidents and events.
Additional materials
Sensor — Network Research & Protection
Polygon — Malware Detonation & Research
Huntbox — Collaborative Hunting & Response Platform
Huntpoint — Behavior Inspection & Host Forensics
Sensor Industrial — Industrial control systems analysis
Solution architecture, integration with traffic and email, typical integration options
Success Stories



Group-IB and Tinkoff
A stronger defense shield thanks to Group-IB’s Threat Hunting Framework Polygon module

Group-IB and AlfaStrakhovanie
Innovative services shielded by Group-IB’s Threat Hunting Framework